CyberSecurity
Cybersecurity is the practice of protecting systems, networks, and programs from digital attacks. CyberSecurity is One of the crucial,
aspect in modern IT Era Our Experts,
have Best and Upto date Architect Solutions.

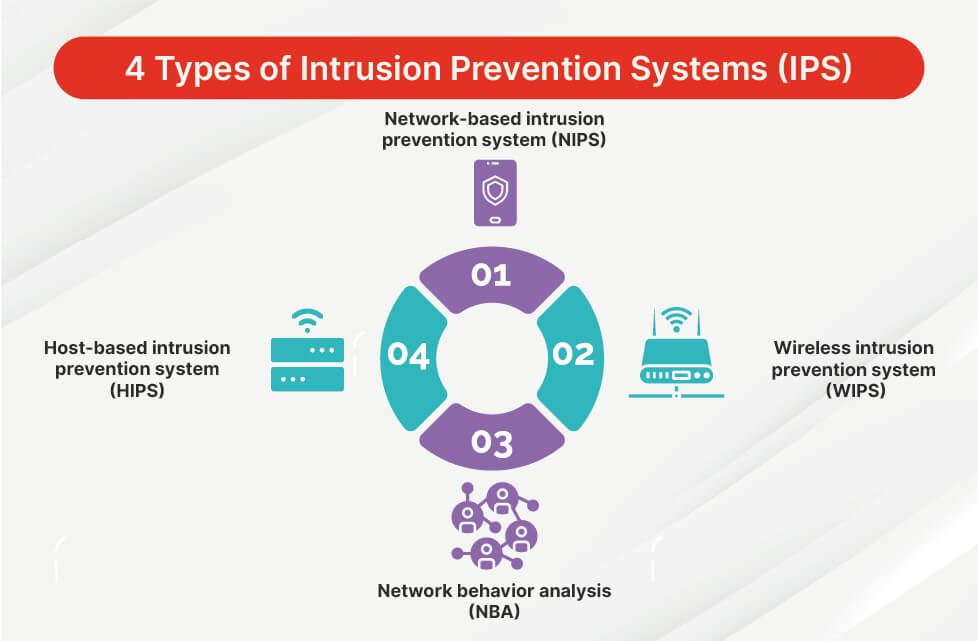
Intrusion Prevention System
An intrusion detection system is a device or software application that monitors a network or systems for malicious activity or policy violations.
Intrusion Detecion System
An Intrusion Detection System (IDS) is a network security technology originally built for detecting vulnerability exploits against a target application or computer.

Remote Infrastructure
Remote Infrastructure management is the remote management of information technology infrastructure. This can include the management of computer hardware and software, such as workstations, servers, network devices, storage devices, IT security devices, etc.
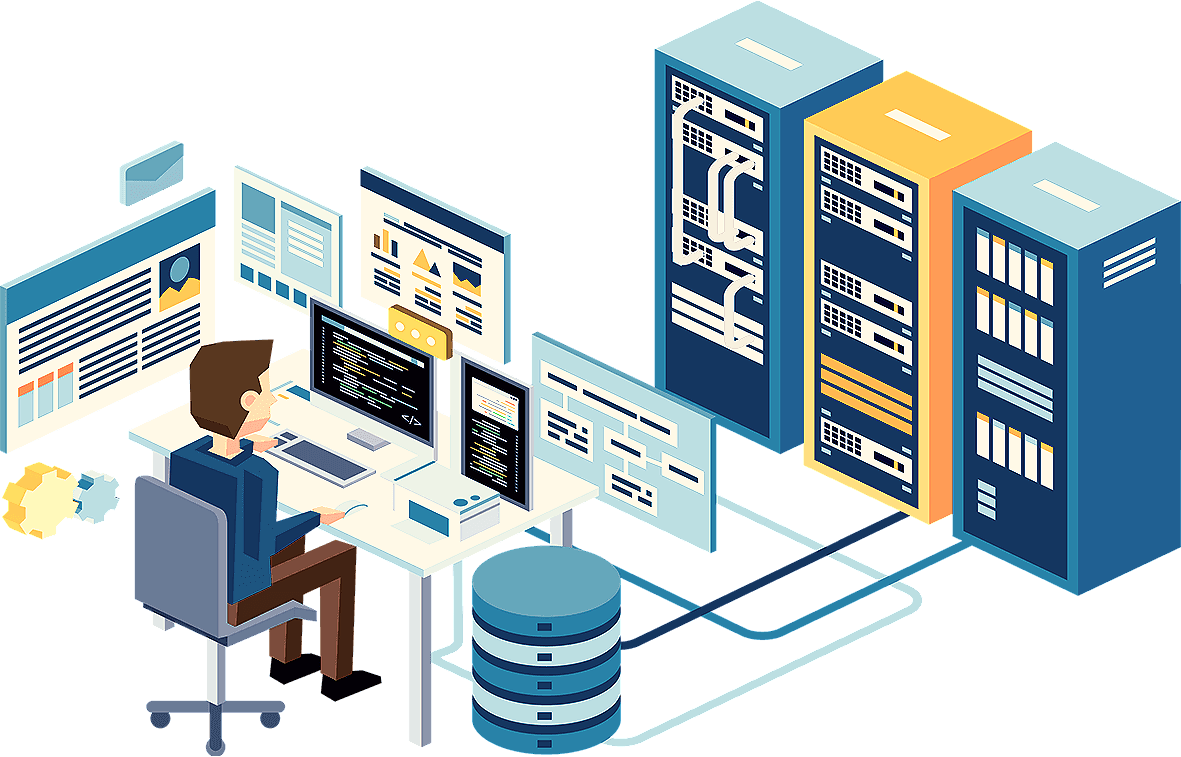
Benefit of Remote Infra Management
The benefits of remote infrastructure management 24/7 monitoring and support. Enhanced security and compliance. Proactive issue resolution. Support for remote work.
Purpose of Remote Infra Management
RIM helps in managing the IT infrastructure centrally with greater coordination and ease of maintenance and reparability.
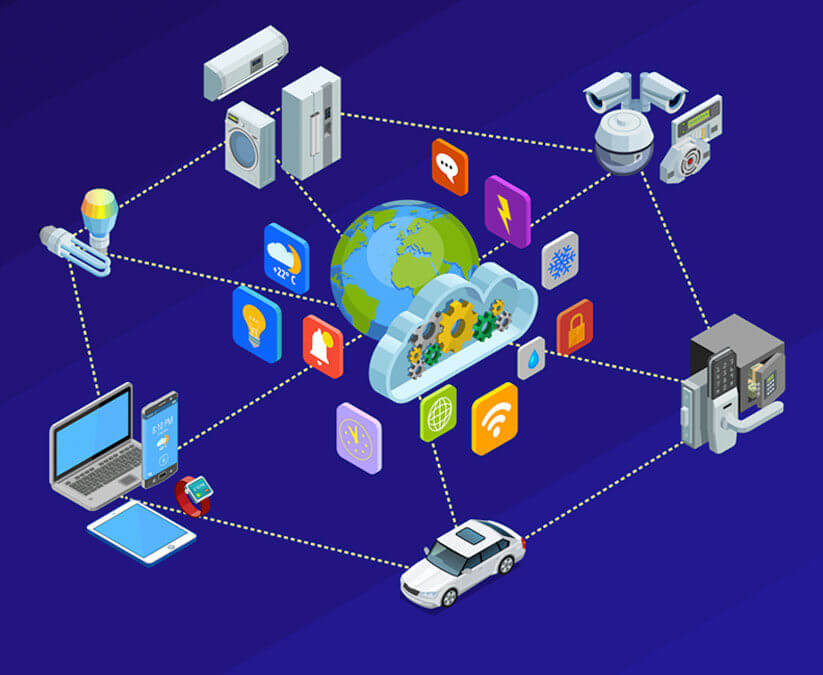
Cloud Services
Cloud service is a platform which encourage industries and organization to transform there infrastructure in digital and make it available 24x7 in all region of world. Cloud services are application and infrastructure resources that exist on the Internet.
Centralized Storage
Centralised cloud computing refers to a model where all cloud resources, including servers, storage, and databases, are managed and housed in a single or few centralised data centers.

Benefits of Cloud Computing
Accessibility anywhere with any device, Ability to get rid of most or all hardware and software, Higher performance and availability, Price-performance and cost savings.
Web Development
Web Development is one of biggest in it era through this we can unlock the various features in modern IT. Its good & effective helps build a strong online presence and helps communicate quality information to your consumers.
Web
Web development can range from developing a simple single static page of plain text to complex web applications, electronic businesses, and social network services.

Web Development Benfits
If you have a website that is well-designed, easy to navigate, and visually appealing, you will be more likely to attract customers than similar businesses that don't have these features.

Data Center Migration
A data center migration is the process of moving select assets from one data center environment to another. It is also referred to as a data center relocation. Data Center Migration is one of the cruical thing now because of every one is trying to get the best and quality compute power by changing their Assets.
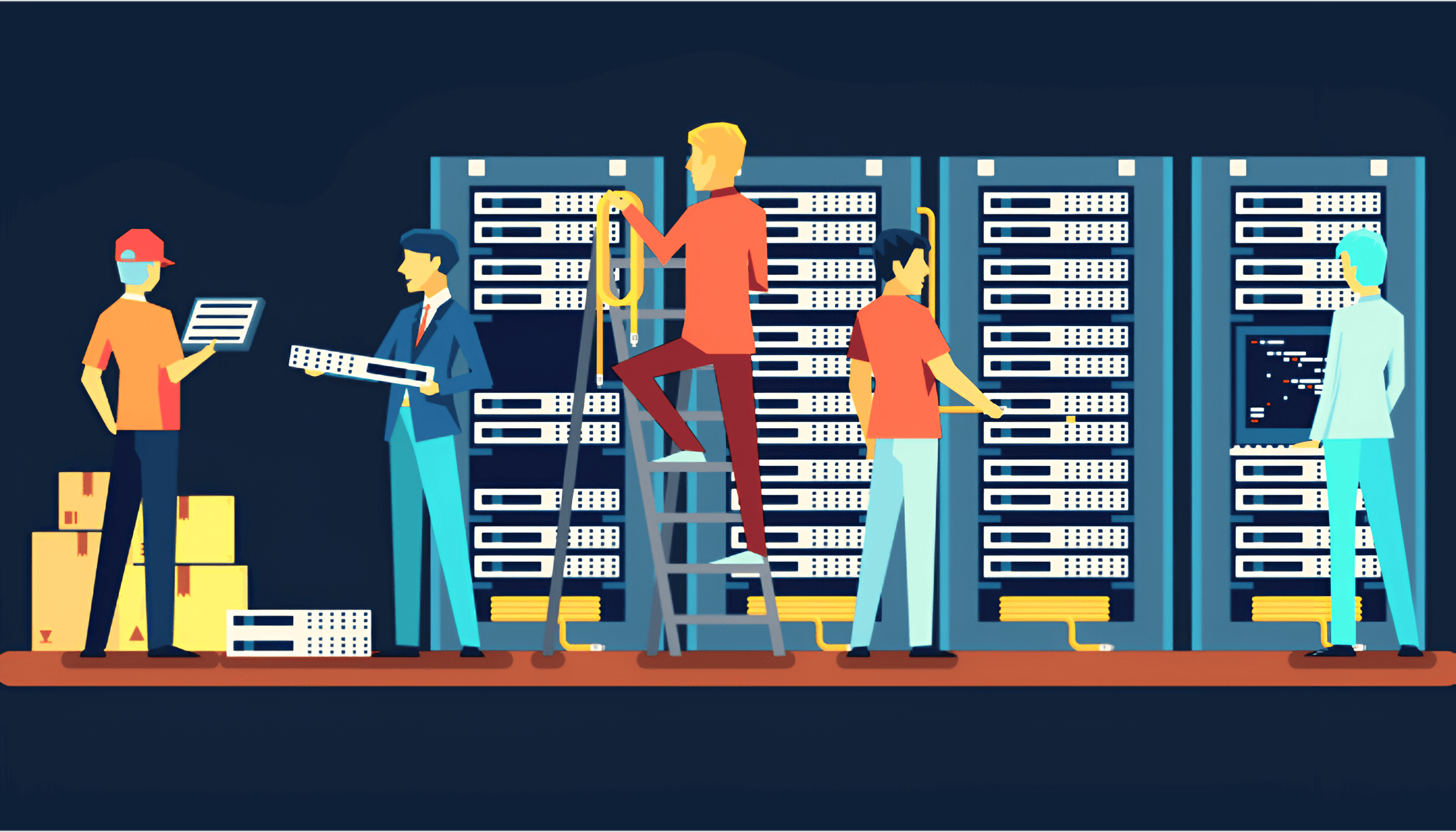
Data center Migration
Migration of Data Center from old Servers and Databases to New Server and Databases Unleashing the Compute power , So that You don't need to face System Failure and your Applications respond perfectly.

Data center Migration to cloud
Migration your data center to cloud. Which is a good advantage now a day plenty of companies are shifting to cloud beacause it's cost saving , faster and no need to care about diseaster recovery.

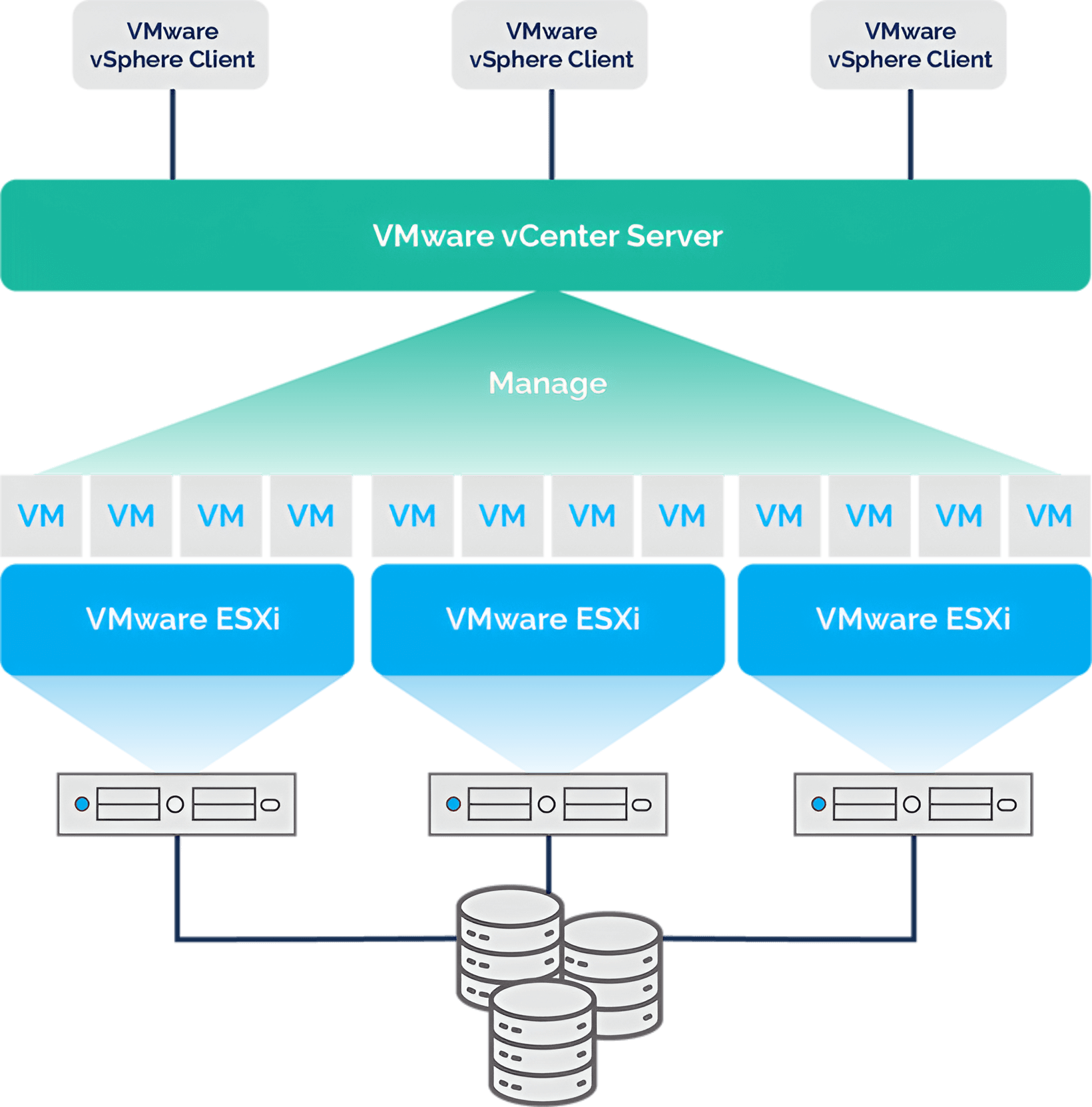
Virtualization
Virtualization is technology that you can use to create virtual representations of physical machines. Virtual software mimics the functions of physical hardware to run multiple virtual machines simultaneously on a single physical machine.
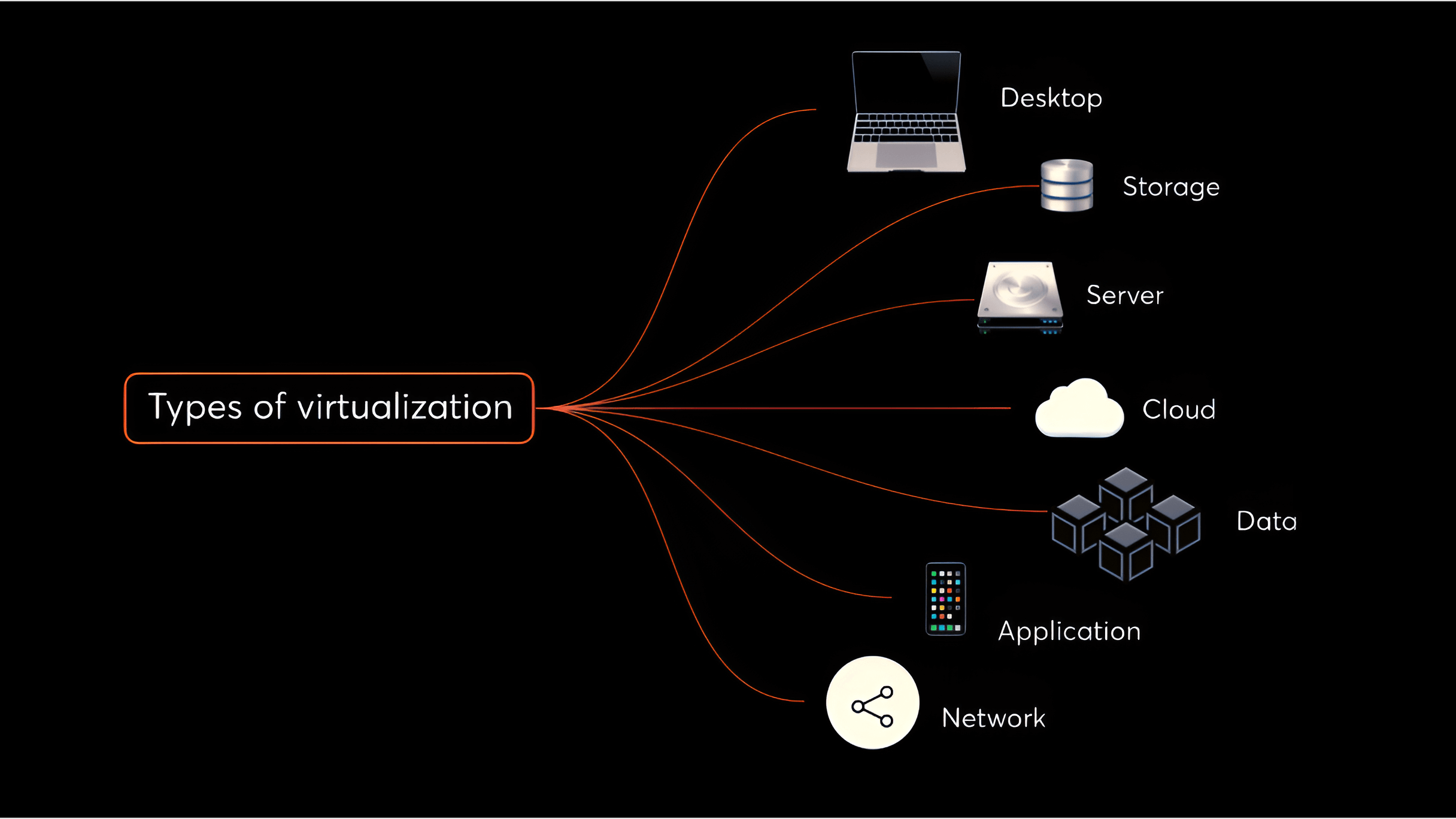
Types of Virtualizaton Virtualizaton
There are many types of virtualization which Benefits to company that takes single sever and create it's virtual copy so we can create storage virtualizaton, Network Virtualizaton, Appliation Viurtualizaton and so on.

Benefits of Virtualization
Virtualization create a virtual copy of our physical server so that we can create multiple instance and can run multiple services with the help of physical server.
.jpg)
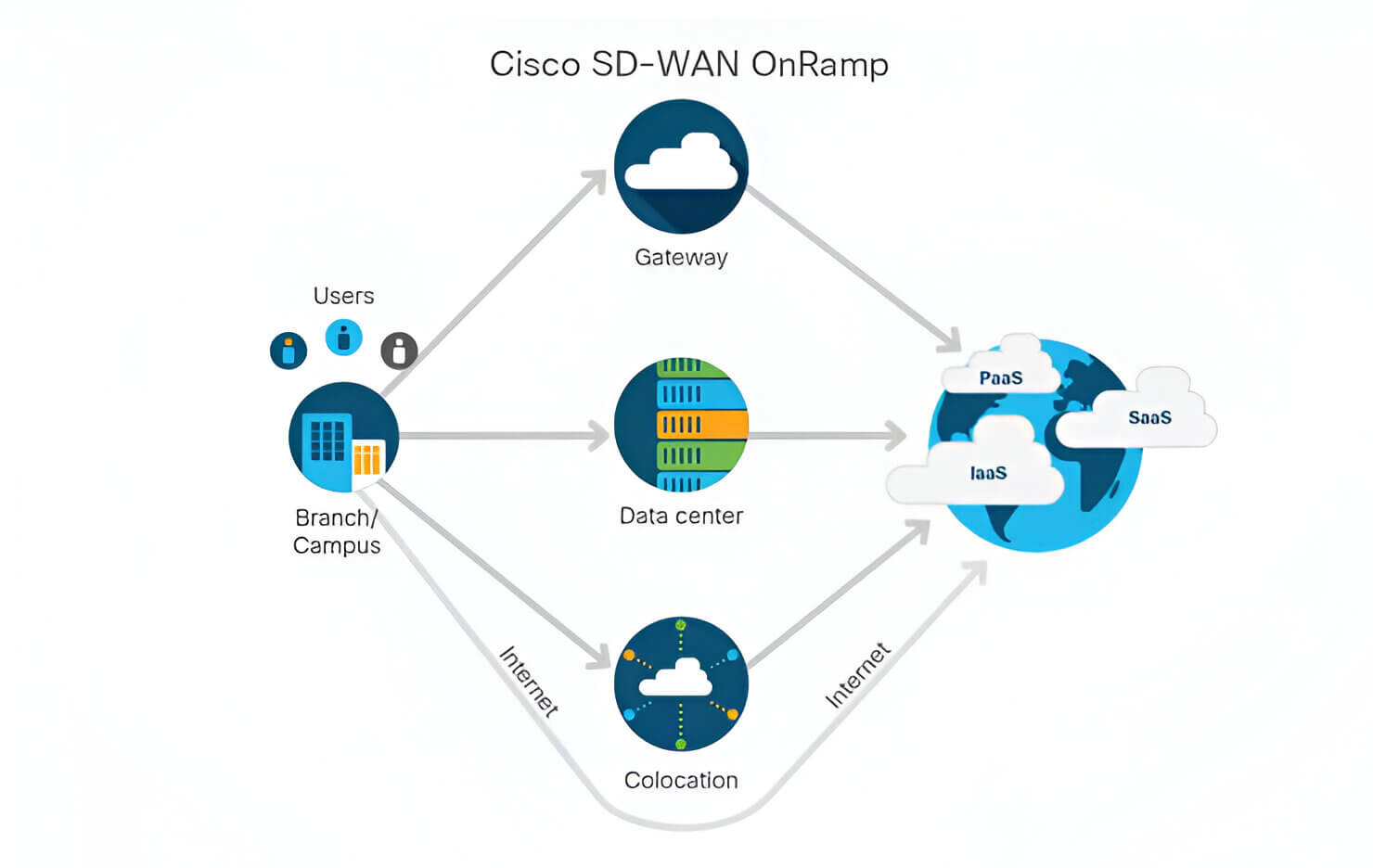
Network Architecture
Network Design is one of the Essential & Perfomance of your network depend upon Network how well you have designed your network, TeamCyber is capable of these things and can give you multiple solution based on your requirements.
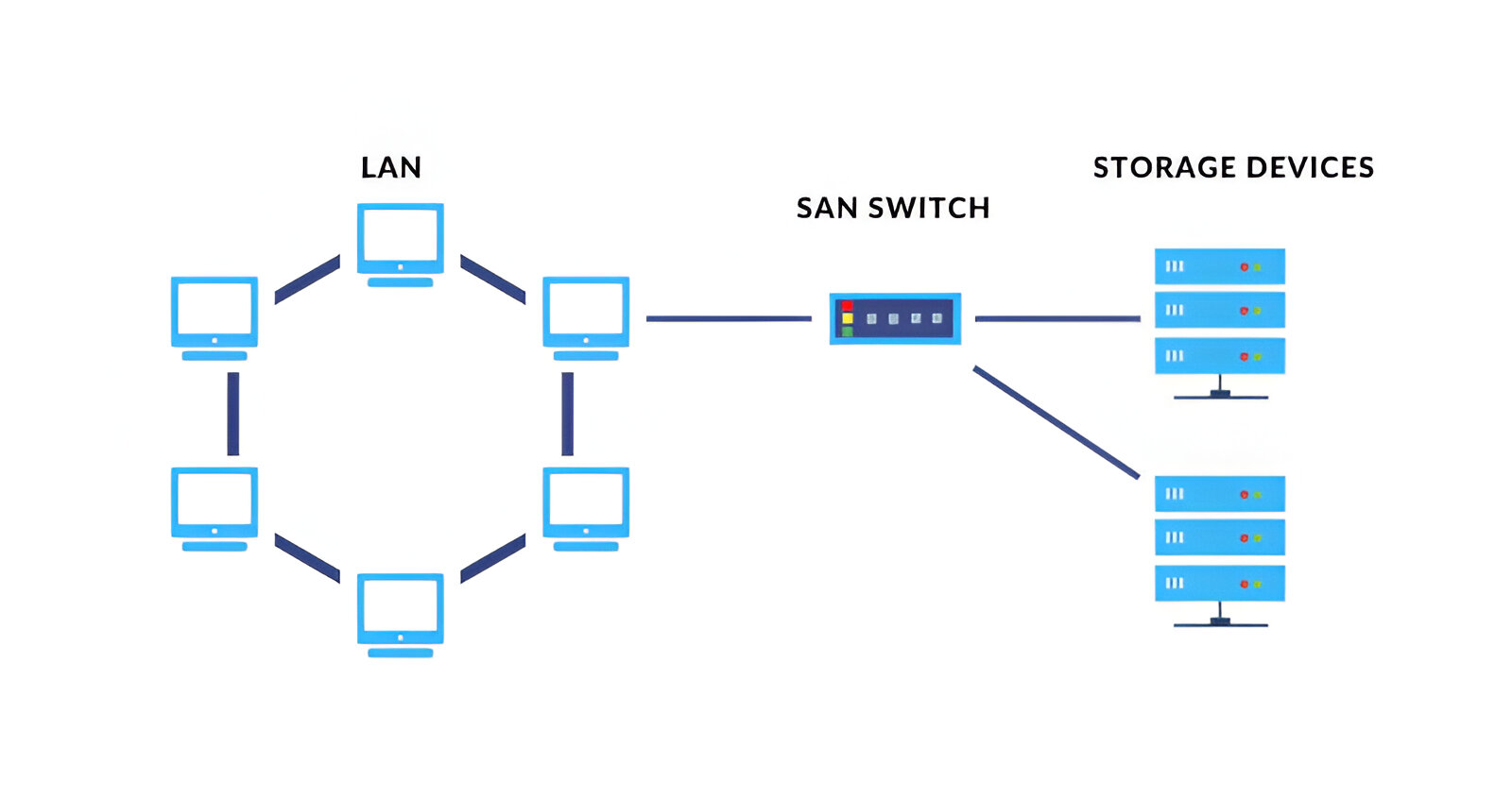
Network Architect
As networks become mission-critical for business functions, design decisions made by IT professionals can have far-reaching implications. It will be more secure and resilient and easier to troubleshoot, and it will scale easily and adapt to future technologies.

Network Design for Securtiy
Network security should be built in during the early design stages, not bolted on later. If security is not factored into the design, incompatible security tools can affect network performance, user experience, and manageability.